
According to SecurityScorecard and The Cyentia Institute, 98% of organizations have a relationship with at least one third party that has experienced a breach in the last two years.
In today’s business world, no organization can survive without relying on business partners to extend its capabilities. However, with service providers getting hit by cybercriminals everyday, making sure that your suppliers understand the potential impact of a cyber attack on their business and the businesses of their customers (including your organization), and implement appropriate mitigations, is a business imperative.
A lot of organizations know this and they conduct vendor due diligence assessments (mostly via questionnaires only) before establishing relationships with suppliers. On the surface, this can be said to be “better than nothing”, but in reality, it is nothing more than a box-ticking exercise for most organizations. On one hand, the time spent conducting this exercise can be better spent to achieve more meaningful business outcomes while on the other hand, yeses by vendors are more likely to lull outsourcing organizations into a false sense of security..
There’s a saying that “no security at all is better than a false sense of it.” If you have no security at all, at least you know and accept that something bad could happen at any time due to your inaction..
Most outsourcing companies end up spending so much time asking questions that are of little value while making their prospective vendors burn productive hours answering these questions. For instance, the Shared Assessments’ Standardized Information Gathering (SIG) tool is commonly used in its default form to obtain responses to security questions from vendors. This tool, which employs industry best practices for gathering and assessing 19 domains of risk, serves as the “trust” component (of “trust but verify”) for outsourcers who wish to use industry-vetted questions on a service provider’s security controls.
The SIG tool comes in two forms: SIG lite and SIG core. The former, which contains 126 questions, is commonly used to assess low-risk vendors or as a preliminary assessment tool during RFI stage while the latter, which contains 855 questions, is used in more detailed assessment to evaluate the security arrangements of organizations who store or manage regulated information.
Lessons from real data breaches
Let’s look at two cases where failure of certain suppliers to implement appropriate security controls led to negative business outcomes for their customers.
How Overby-Seawell cost KeyBank more than $5 million in damages
When KeyBank lost the personal data of its consumers to cybercriminals in July 2022, it was primarily due to the failure of Overby-Seawell, its key supplier, to design and implement appropriate safeguards around the collection and maintenance of highly sensitive and confidential mortgage information. This breach, which ended up costing KeyBank in excess of $5 million in damages, is a reminder of how a third party supplier can introduce a security weaknesses into an organization’s cyber defense chain.

It is difficult to tell whether KeyBank had a vendor risk management function in place prior to this data breach, but it is fair to assume that one of the biggest 25 banks in the US would have conducted some sort of due diligence on a prospective key supplier before establishing business relationship.
Typically some of the questions asked during such due diligence exercise would have been similar to the following:
1. Are security controls for handling personally identifiable information applied?
2. Is personally identifiable information handled in accordance with relevant legislation throughout its lifecycle?
3. Does the organization assess the impact of business information being disclosed to unauthorized individuals?.
If KeyBank had asked these questions in the course of a vendor due diligence exercise and Overby-Seawell had responded “yes” to them all, then what? These are all great questions, but most of the time, the organization conducting the assessment does very little by way of validating the existence and/or effectiveness of relevant security controls.
How attack against a fourth-party vendor can be a problem
When Healthcare giant, Highmark Health, was held responsible for leaking healthcare data of over 60,000 individuals in March 2022, it was as a direct result of its relationship with WebbMason, its provider of marketing services. However, the attackers did not get that data directly from WebbMason. Instead, they targeted Quantum Group, a printing and mailing services provider used by WebbMason. The files accessed by the hackers related to provider mailings regarding prescription drug changes, including names, birth dates, Highmark member IDs, and prescription information.
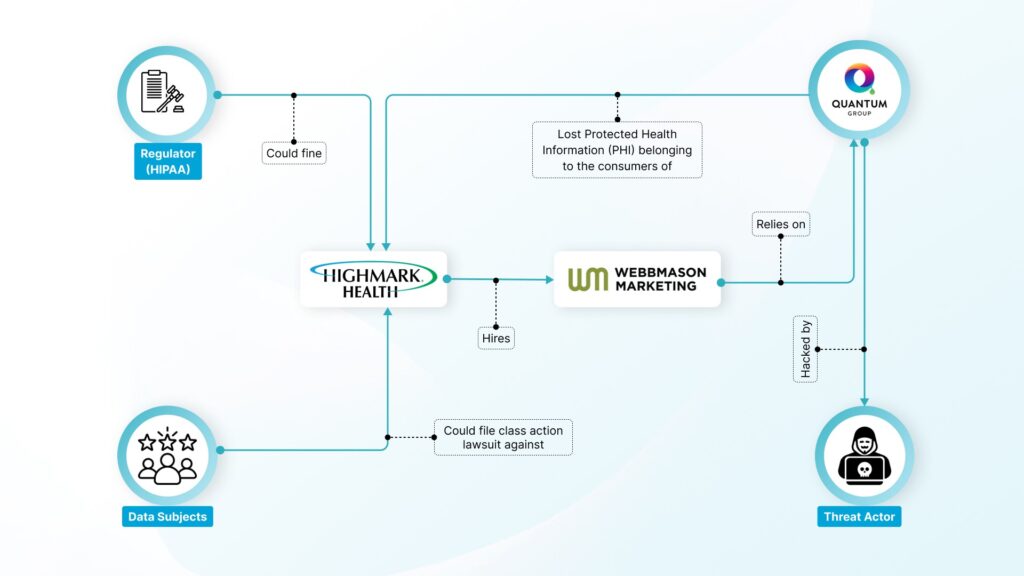
While we may not know anything about the level of due diligence conducted by Highmark Health on WebbMason, and by WebbMason on Quantum Group, one can argue that Highmark Health may not have anticipated that a vendor of its vendor could be responsible for a major breach of its consumers’ healthcare data.
How many organizations ask questions about the information security arrangements of the key suppliers of their prospective vendors? How are the answers to those questions validated?
While conducting vendor risk assessments, organizations who control regulated data need to remember that they also have the duty of due care in addition to their duty of due diligence. For instance, under the EU General Data Protection Regulation (GDPR), a data controller (entity in control of data processing) and a data processor (any third party that works on behalf of the data controller) have different levels of compliance obligations.
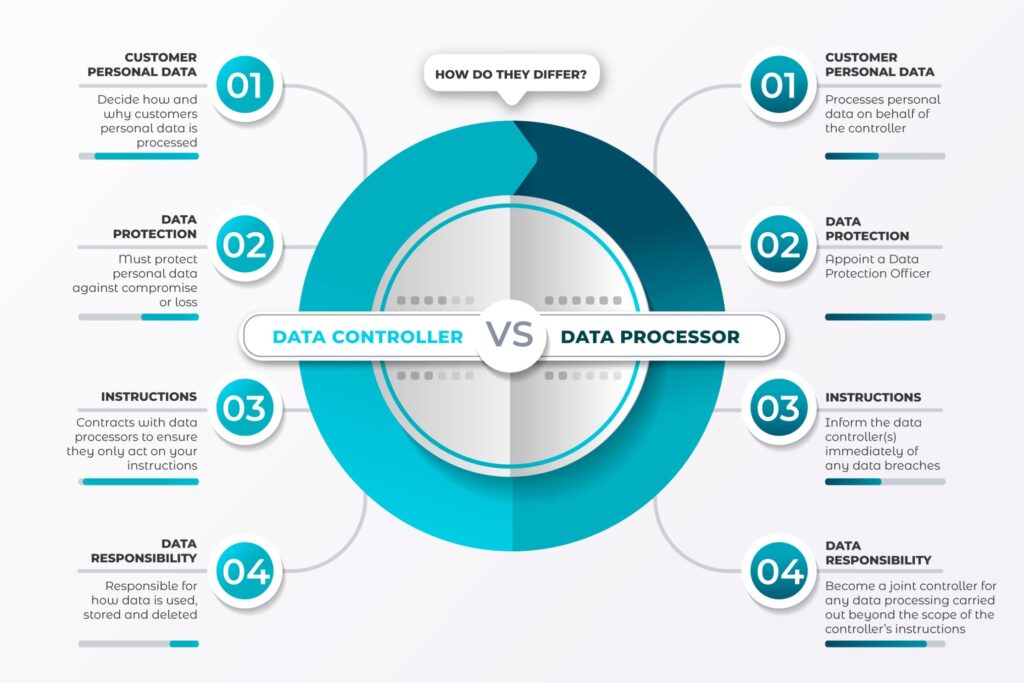
Although these entities should still take appropriate organizational and technical measures to ensure that any processed data is done so in line with the GDPR. Should a data breach occur, the regulatory hammer will come down heavier on the data controller than it will on the data processor because the controller hires the processor, and so have the overall say and control over the reason and purposes behind data collection and the means and method of any data processing.
One of the key lessons to be learned from the Highmark Health breach is that organizations need to be aware of the information security arrangements of the sub-processors (e.g., Quantum Group) leveraged by the entities working on their behalf (e.g., WebbMason) to process personal data of their consumers. If you ask your vendor the right question about their key supplier and demand proof, you’re essentially telling them where to go get the answers from. If the answer or proof is not satisfactory, then you have a risk treatment decision to make.
So what should organizations do to cover their bases when it comes to vendor risk assessment? Below are five important things to bear in mind when assessing the risk posed to your business by a vendor:
1. Always ask your vendors the right questions about the security practices of their vendors who may be touching your data. Remember, the keyword is “vendor”, not “third-party”. The fact that you do not have a direct relationship with the vendors of your vendor does not mean that you cannot positively influence their information security arrangements
2. Don’t just send your vendors generic questions to answer. With your cybersecurity risk appetite in mind (hopefully, you have a risk appetite statement), tailor your questions in accordance with the services to be provided by individual vendors.
3. Hold your vendors to your own policies and standards. Why send a bunch of questions in spreadsheets when you already have policies and standards that underlie your organization’s approach to information security? Derive your questions from relevant internal policies and standards. Understand that any IT environment where your sensitive data is housed is an extension of your network.
4. If you already leverage the services of vendor risk management solutions providers such as Security Scorecard, BitSight and Upguard, you’re doing well, but do not stop at that because those security ratings don’t always tell the full story. Complement that with point #3 above and manual validation of the strengths and flaws reported by these risk scoring platforms.
5. A one-off, annual assessment is also outdated. Maintain situational awareness of the risks posed to your organization by your vendors (and their vendors) through continuous monitoring of their external attack surface, and remember them as you go about your cyber threat intelligence activities. They are a key part of your cyber defense universe.
The foregoing list is not exhaustive but it’s a very good start. The cyber threat, regulatory and technology environments have evolved beyond the days of questionnaires that lack any distinguishing characteristics. Your vendors are capable of allowing cyber adversaries into your network through the backdoor. Help them shut the door by complementing your duty of due diligence with that of due care.

Written By Mobolaji Moyosore.
Cyber security thought leader with 20 years of cross-sector & cross-continental experience building and sustaining cyber-resilient infrastructures.