Experience Full Stack Cyber Defense Support
We are your extended cyber security team providing business-aligned advisory, professional and managed services to support your cyber security program. Our business focused security professionals work round the clock to keep your cyber adversaries at bay.

SUMMARY OF SERVICES
Below are some of the job functions performed by Digiss under the full stack cyber defense support agreement

Endpoint Protection
- Ensuring deployment and correct functioning of client’s EDR solution on every managed device
- Hunting for hidden cyber threats through real-time and historic retrospective search and analysis
- Vendor liaison, platform support, and ongoing policy configuration and protection enhancement

Incident Detection and Response
- Leveraging highly qualified and experienced SOC analysts to provide 24/7/365 operation
- Conducting tailored cyber threat intelligence on behalf of our clients
- Taking on the operational burden of vulnerability discovery, analysis, and reporting to help client focus on remediation efforts

Infosec Governance, Risk and Compliance
- Supporting annual security assessments, compliance, certifications, and audit readiness efforts
- Leading vendor security risk management efforts and ongoing monitoring of high-risk vendors
- Managing client’s information security risks, controls gaps, risks register and cyber security exceptions

End-User Security Awareness
- Developing and championing a risk-driven security awareness program
- Aligning security awareness program with business requirements
- Designing and conducting outcome-focused phishing simulations with a view to driving down click rates
- Promoting positive cyber security behavior periodically through carefully crafted newsletters and advisories

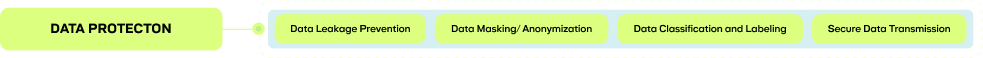
Data Protection
- Implementing and managing data protection measures, including encryption, access controls, and data masking, to ensure that sensitive data is secure
- Identifying and addressing vulnerabilities in data systems and databases through regular scans and assessments.
- Implementing and operating security tools and mechanisms to protect data at rest, in use and in transit.
- Maintaining documentation related to data security policies, procedures, and incident reports

Security Design Architecture
- Designing and developing security controls, patterns, and strategies to identify and address gaps in deployed infrastructures and other enterprise solutions
- Leading the design, development, and implementation of the organization’s technical security architecture
- Supporting availability, performance and capability enhancements of existing security technologies

Security Engineering
- Selecting, deploying, and managing security tools and software on endpoint devices, such as encryption software, endpoint detection and response (EDR) solutions, and mobile device management (MDM) systems
- Supporting availability, performance and capability enhancements of existing security technologies
- Managing and configuring access control mechanisms to limit who can access, modify, or delete data.
- Configuring and managing logging and monitoring to detect and respond to security events.
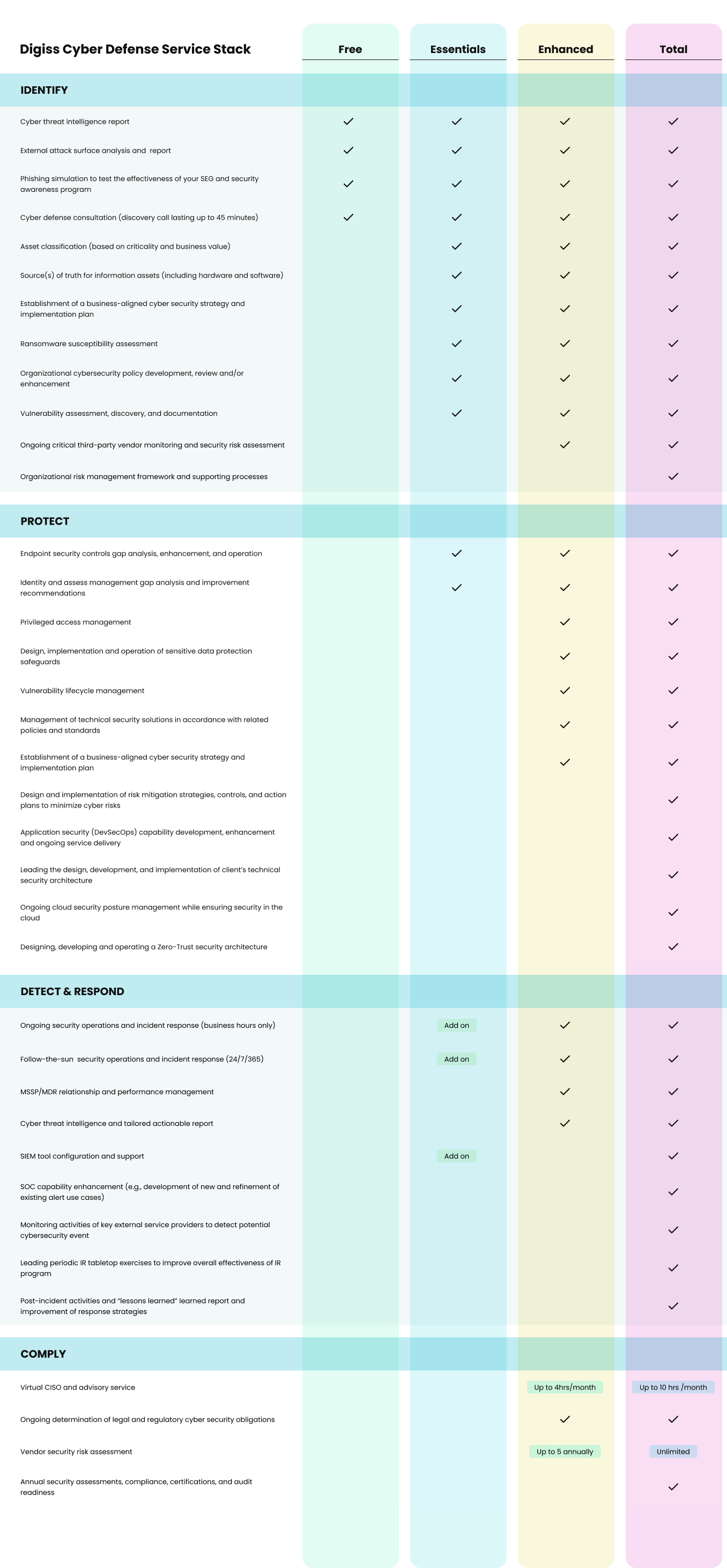
CAPABILITY MAP
The capability map below shows major activities that are associated with each of the twelve (12) cyber security domains covered under our cyber defense support agreement.







CYBER DEFENSE SERVICE STACK
The capability map below shows major activities that are associated with each of the ten (10) cyber security domains covered under our cyber defense support agreement.