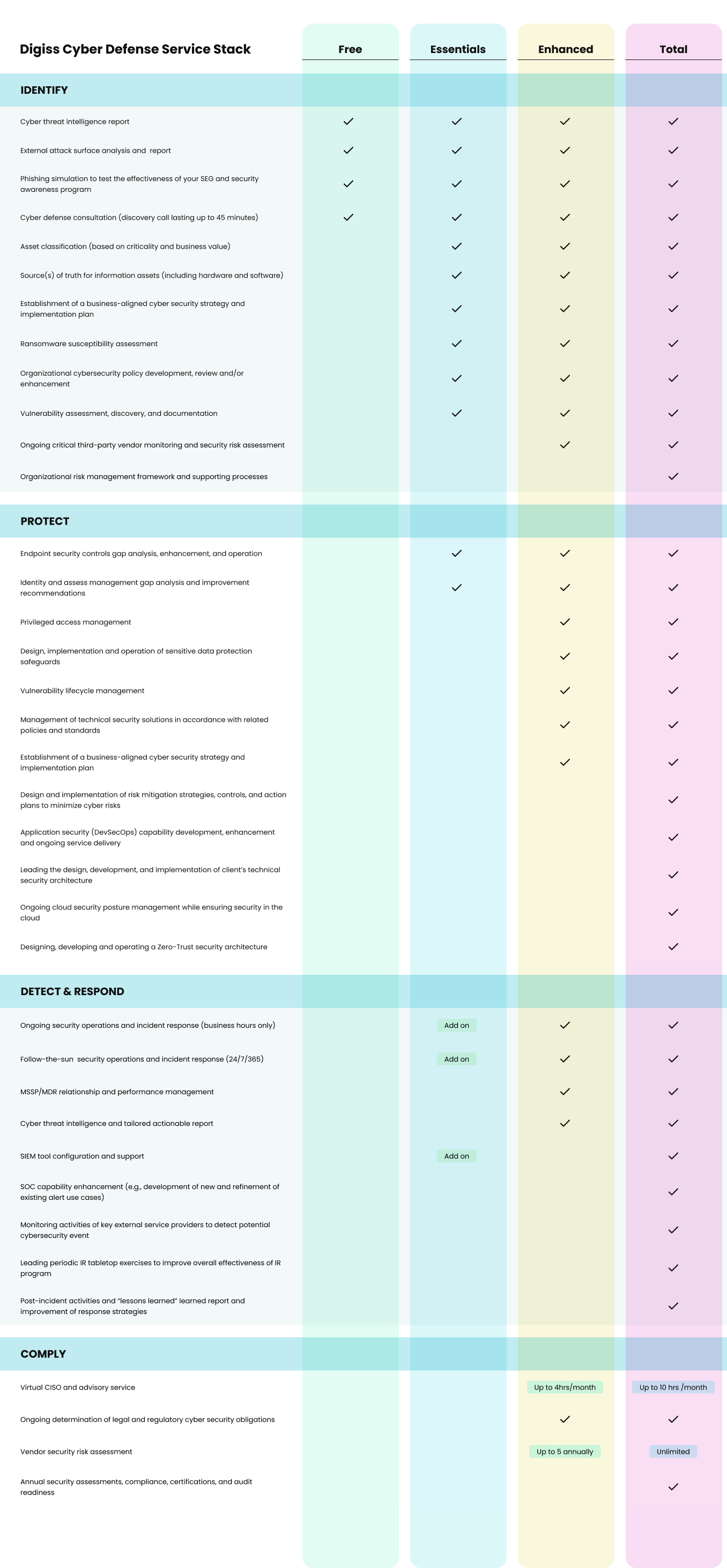
Cyber Defense Service stack
The capability map below shows major activities that are associated with each of the ten (10) cyber security domains covered under our cyber defense support agreement.

CAPABILITY MAP
The capability map below shows major activities that are associated with each of the twelve (12) cyber security domains covered under our cyber defense support agreement.







CYBER DEFENSE SERVICE STACK
The capability map below shows major activities that are associated with each of the ten (10) cyber security domains covered under our cyber defense support agreement.
Our Technology Partners